Do you always turn WiFi off on your smartphone before leaving the house or work? You might think there's no harm in having WiFi turned on but not connected to a network, but that's not necessarily the case.
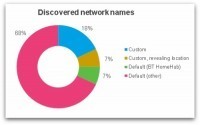
A wireless device goes through a discovery process in which it attempts to connect to an available wireless network. This may either be ‘passive’ - listening for networks which are broadcasting themselves - or ‘active’ - sending out probe request packets in search of a network to connect to.
Most devices use both passive and active discovery in an attempt to connect to known/preferred networks. So it's very likely that your smartphone is broadcasting the names (SSIDs) of your favourite networks for anyone to see.
===> An ‘evil twin’ attack could even accomplish this without needing any knowledge of your WiFi password - very damaging for all of those who use mobile banking for instance! <===
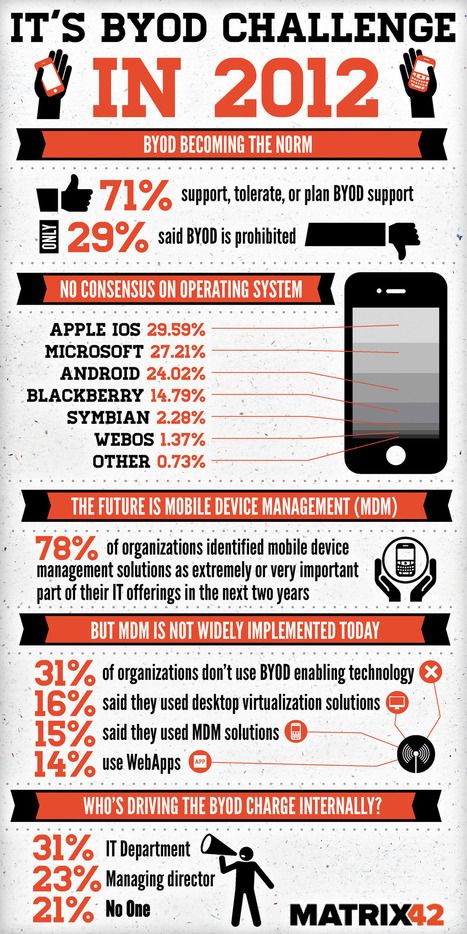
Gust MEES: a MUST READ for anyone using m-Learning + "BYOD" and also any smartphone user...



 Your new post is loading...
Your new post is loading...