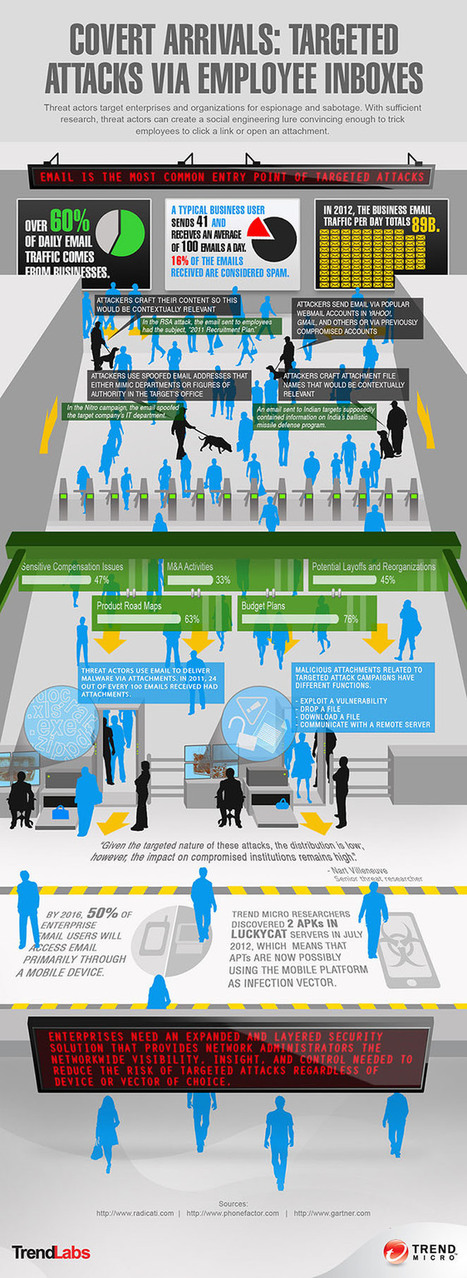
Hackers accessed the credit card information of tens of thousands customers of the University of Michigans Union Ticket Office, the latest organization that has fallen victim to a breach affecting a thirdparty vendor.
Hackers accessed the credit card information of tens of thousands customers of the University of Michigan's Union Ticket Office, the latest organization that has fallen victim to a breach affecting a third-party vendor.
How many victims? More than 33,000.
What type of personal information? Names, street addresses, email addresses, phone numbers, credit card numbers and expiration dates.
What happened?
The database supplied by third-party ticketing solution provider Vendini was compromised by hackers who may have stolen the personal information of any U of M customer in the last two years.
What was the response? University officials have contacted all individuals affected by the breach.
Details: How the hackers were able to compromise the Vendini systems is currently unknown. According toa statement released by the company, the stolen information does not include credit card security access codes, account user names or passwords.



 Your new post is loading...
Your new post is loading...







![Protecting Your Password - How Hacker Friendly is Yours [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/_2G3yRb429iCkAsLUS3C0Dl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)


![BYOD: Bring Your Own Risk (BYOR) [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/y5NTg9uYlSpK6x67Mbb7WDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






![Mobile Threat in Action [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/cJttrx6XoZpu_ERcpy9jUjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



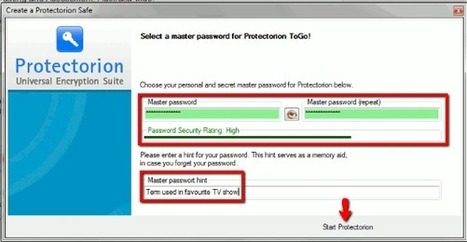



Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=LinkedIn