Share this news now.Share this news now.In a cybercrime ecosystem populated by commercially available WordPress brute-forcing and mass vulnerable WordPress installation scanning tools, cybercriminals continue actively capitalizing on the platform’s leading market share within the Content Management System’s market segment.
Successfully exploiting tens of thousands of installations on a daily basis, for the purpose of utilizing the legitimate infrastructure to achieve their fraudulent/malicious campaign objectives, the tactic is also largely driven by the over-supply of compromised/accounting data, usually embedded within sophisticated Web-based attack platforms like the ones we’ve profiled in the past.
We’ve recently intercepted a malicious campaign exclusively relying on rogue WordPress sites, ultimately serving client-side …Share this news now.



 Your new post is loading...
Your new post is loading...





![Cisco: The Biggest Mobile BYOD Deployment Around? [Slides] | 21st Century Tools for Teaching-People and Learners | Scoop.it](https://img.scoop.it/979Kz0MNTSPBQDYgcyqzhzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






![Mobile Security Firm Analyzes 1.7 Million Android Apps [Infographic] | 21st Century Tools for Teaching-People and Learners | Scoop.it](https://img.scoop.it/-U8bVTIhWiIVeL-h7oriNjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

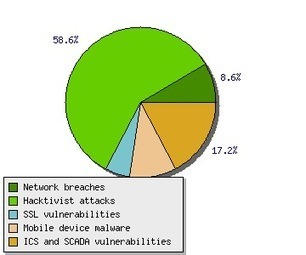



Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=WordPress
- http://www.scoop.it/t/wordpress-annotum-for-education-science-journal-publishing/?tag=WordPress-Security