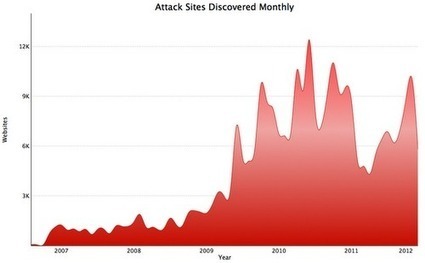
Google has shared some interesting Web security statistics, and while the information was not published as an official “threat report”, the company has provided some insight into the growth of malicious activity across the Web.
he company provides a free and public Safe Browsing API that allows other organizations to keep their users safe by using the data Google has compiled.
• Google said it discovers about 9,500 new malicious websites every day – These sites could be either innocent sites that have been compromised by cybercriminals, or purpose-built sites designed for malware distribution or phishing.
• Approximately 12-14 million Google Search queries per day show warnings in order to caution users from going to sites that may be compromised.
• Google provides malware warnings for about 300,000 downloads per day through its Chrome download protection service.
• Google also sends thousands of notifications daily to Internet Service Providers (ISPs) & CERTs to help them keep their networks clean.
Read more:
http://www.securityweek.com/google-produces-informal-web-threat-report-shares-insights
Via
Gust MEES 


 Your new post is loading...
Your new post is loading...



![Yet another iPhone lockscreen vulnerability. This time in iOS 7.02 [VIDEO] | Aprendiendo a Distancia | Scoop.it](https://img.scoop.it/boKnUeA0iZ0rIALHJ2F8kzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



![BYOD Security Issues [Infographic] | Aprendiendo a Distancia | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)




![Are You Safe Online? [INFOGRAPHIC] | Aprendiendo a Distancia | Scoop.it](https://img.scoop.it/1G_5cqxnwyPNa-B3nFCNbDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)
![How to Avoid 17 Internet Scams [INFOGRAPHIC] | Aprendiendo a Distancia | Scoop.it](https://img.scoop.it/rAUu9hiWLA6h_bZS-utdfTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)


If you bring your phone, tablet or laptop with you when you travel, there’s one thing to keep in mind: public WiFi networks are public.
“That open Wi-Fi connection opens the door for hackers,” writes NPR’s Steve Henn. “They can get in the middle of transactions between, say, you and your bank.”
Because you’re sharing the network with strangers, there’s the risk that someone is using readily available software that snoops on what you’re doing.
Learn more:
- http://gustmees.wordpress.com/2013/05/27/dangers-of-wifi-in-public-places/
Really useful information to remember when you are travelling and using free wifi. Take care that you understand what you are using and stay safe.
If you bring your phone, tablet or laptop with you when you travel, there’s one thing to keep in mind: public WiFi networks are public.
“That open Wi-Fi connection opens the door for hackers,” writes NPR’s Steve Henn. “They can get in the middle of transactions between, say, you and your bank.”
Because you’re sharing the network with strangers, there’s the risk that someone is using readily available software that snoops on what you’re doing.